The Irish Data Protection Commission (DPC) has released its DPIA Blacklist highlighting processing activities which require a DPIA and its Activity Report detailing the frequency of complaints and breaches reported. Additionally, Mazars in association with McCann FitzGerald conducted their third GDPR survey, which provides interesting insights into GDPR from an Irish business leaders perspective.
DPC activity report
The DPC’s activity report for the first half of 2018 (pre-GDPR) was published on the 23 November 2018, highlighting a lot of great insights for Irish businesses. The two activities we are most interested in: complaints received and audit findings.
Audit Findings
In the first half of 2018, 23 audits were carried out. These audits take place on a strategic basis guided by complaints received.
The main themes of these audits:
- Retention of Electronic and Manual Data
Many organisations are implementing the physical aspects of their retention policies but continue to hold data electronically. Informally, the DPC has highlighted the need to invest in data mapping to fully implement retention and adhere to erasure requests. - CCTV Policies
Organisations employing CCTV need a robust CCTV policy detailing purposes, justifications, locations, access rights and requests, retention and disposal. - Cookies
Under S.I. 336 of 2011 the minimum requirement for websites which operate cookies is a clear and comprehensive communication regarding the purposes to which they must consent and a clear means of giving or refusing consent is required. Users must be able to withdraw this consent, and the onus is on the organisation to demonstrate that the user has provided consent. - Collection of PPSN
Many entities have a legitimate reason to request an individual’s PPSN, for a range of purposes. However, it is critical that this PPSN is not collected where it is not required by the controller. - Data Sharing Agreements
Organisations need to review all information sharing agreements in place to ensure they are in compliance with the GDPR and the Data Protection Act, 2018
Complaints received
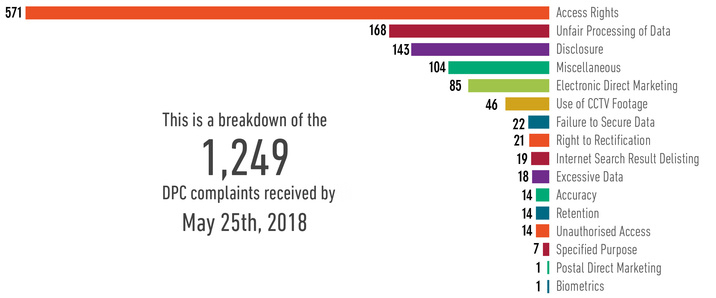
By the May 25th, the DPC had received 1,249 complaints, a breakdown of which is provided below. This indicates that the number of complaints received by the DPC in 2018 is set to match 2017, where 2,642 complaints were received.
GDPR survey key findings
Our third GDPR survey, in association with McCann Fitzgerald, was published this month. While we have observed that many leaders have increased confidence in their ability to reach a material level of compliance in comparison to 2017, we are also seeing a rise in expressed difficulties around areas such as demonstrating compliance, consent mechanisms and privacy notices as well as assessing and documenting privacy risks. This is not surprising as it shows respondents are becoming increasingly knowledgeable and have a growing awareness of the stringent obligations introduced by the GDPR.
DPIA blacklist
The DPC published their adopted blacklist, following a public consultation and approval by the European Data Protection Board, on 15 November 2018.
This blacklist details processing activities which require a Data Protection Impact Assessment (DPIA), in line with Article 35 of the GDPR.
- Use of personal data on a large-scale for a purpose(s) other than that for which it was initially collected pursuant to GDPR Article 6(4).
- Profiling vulnerable persons including children to target marketing or online services at such persons.
- Use of profiling or algorithmic means or special category data as an element to determine access to services or that results in legal or similarly significant effects.
- Systematically monitoring, tracking or observing individuals’ location or behaviour.
- Profiling individuals on a large-scale.
- Processing biometric data to uniquely identify an individual or individuals or enable or allow the identification or authentication of an individual or individuals in combination with any of the other criteria set out in WP29 DPIA Guidelines.
- Processing genetic data in combination with any of the other criteria set out in WP29 DPIA Guidelines.
- Indirectly sourcing personal data where GDPR transparency requirements are not being met, including when relying on exemptions based on impossibility or disproportionate effort.
- Combining, linking or cross-referencing separate datasets where such linking significantly contributes to or is used for profiling or behavioural analysis of individuals, particularly where the data sets are combined from different sources where processing was/is carried out for different purposes or by different controllers.
- Large-scale processing of personal data where the Data Protection Act 2018 requires “suitable and specific measures” to be taken in order to safeguard the fundamental rights and freedoms of individuals.
Breach reporting
As we mature in our capability to accurately assess the level of risk associated with security incidents and data breaches, we are becoming increasingly aware of the fact that many organisations in Ireland are overreporting—a sentiment which is shared with the DPC.
In response to breach notifications, we are seeing the DPC remind organisations of situations where breaches are likely non-reportable. Looking back to the Article 29 Working Party guidance on data breaches, we are reminded of the following such situations:
- Where individuals are not easily identifiable: if the breached data is encrypted to an appropriate level such that the data subject(s) will be unintelligible, the likelihood of a risk to the data subject(s) will be reduced.
- Disclosure to trusted individuals: if personal data is accidentally disclosed to a ‘trusted’ individual – such as the wrong department of an organisation or to a commonly used supplier – the controller can request that the data be returned or securely destroyed.
Where the controller knows this individual, their procedures and relevant details, the controller may have a reasonable level of assurance that the third party shall not read or access the data which was sent in error and will comply with instructions to return/destroy it.
Note: This should be considered on a case-by-case basis, and in certain scenarios, a likely risk may still be present, rendering the breach reportable to the DPC.
Cyber insurance
The increased financial and reputational damage associated with cyber security instances which become personal data breaches has put cyber insurance on the agenda of management boards across the country. A conglomerate of insurance boards have released a paper to aid organisations in preparing for cyber insurance.
This paper highlights the need to consider the extent of exposure to sensitive data the organisation has when taking out a cyber insurance policy. What does paper doesn’t explicitly cover is type of cyber insurance which will cover organisations in the event of a sanction from the supervisory authority (the DPC) or the cost of securing a major data breach. This article from AIG is very useful and details the elements of GDPR which AIG deems to be insurable, namely:
- Covering fines, to the extent that they will be coverable by law (this will need to be tested in the courts).
- Covering the costs of responding to breaches which involve large volumes of data/consume large amounts of time.
- Defence costs and liability claims in the event that data subjects suffer material or non-material damages as a result of a data breach.
An interesting point which is not stressed here is the need to cover indemnity clauses in data processing situations if an organisation has indemnified another in the event of a data breach. Or in situations where a processor has not agreed to indemnify the data controller, should they cause a data breach.