With ransomware attacks on the increase, Irish businesses must take all precautionary measures to protect network, systems and information from this type of cyber-crime. Furthermore, an organisation must be prepared to triage, investigate, contain, eradicate, and recover from a ransomware attack, should it materialise.
Significant ransomware attacks
14 May 2021 A vicious ransomware attack, which is likely the most significant cybercrime attack on the Irish State, resulted in the Health Service Executive (HSE) temporarily shutting down its IT system. This affected patient hospital appointments and all national and local systems involved. Significant disruption occurred with routine appointments cancelled, including cancer, maternity check-ups, radiotherapy, X-ray and MRI scans, specific treatments and administrative procedures1. |
7 May 2021 A ransomware attack impacted the network of the US energy operator Colonial Pipeline disrupting operations and the wider oil supply chain. It is believed to be one of the largest attacks on the US. The 8,900km pipeline usually carries 2.5 million barrels a day on the East Coast. The closure saw diesel supplies, petrol and jet fuel tighten across the US and prices rising. Cyber-criminal gang DarkSide reported having been paid the $5m (€4.2m) ransom by Colonial Pipeline2. |
12 May 2017 Four years ago, WannaCry ransomware malicious code took advantage of unpatched systems that affected 200-000-300,000 computers globally with billions of damages reported. It is estimated that the National Health Service (NHS) was impacted by the cancellation of 19,000 operations and appointments. This attack affected many sectors, including health, transportation, government departments, banks and car manufacturers. |
Bringing business critical systems back online affected by ransomware takes time. It can take several days or weeks and typically involve external security experts investigating ransomware incidents to determine the extent of damage and compromise of sensitive data.
What is ransomware?
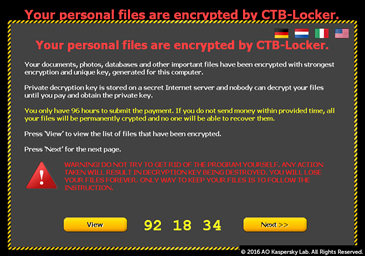
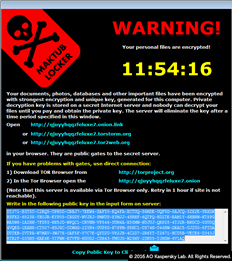
Ransomware has been around for the last decade, but what exactly is ransomware? It is a type of malware that prevents you from accessing your computer and encrypts personal data, files and folders (documents, spreadsheets, pictures, and videos). A cyber-criminal will then demand a ransom payment to return the files and folders to you.
How can you get ransomware on your computer?
A ransomware attack is typically delivered via an email attachment like an executable file, an archive or an image. It can also get onto your computer via infected USB stick, or portable devices, phone or through visiting a compromised/exploited website. Once the attachment is opened or a user visits the compromised site, the malware is released into the system.
How does a ransomware attack work?
The infection is not immediately apparent to the user. The malware operates silently in the background until the system or data-locking mechanism is deployed. Then a dialogue box appears that tells the user the data has been locked and demands a ransom to unlock it again. By then, it is too late to save the data through any security measures3.
See below a couple of screenshot examples
What is a cybercriminals motivation for attack?
Cybercriminals are often motivated by money and tend to attack pipelines or the likes of banks or organisations who can afford to pay the ransom. The attack on the Irish Health system is recognised as a malicious act, performed by cybercriminals that have no regard for the impact on patients or children who need access to essential medical services.
How do cybercriminals get paid?
The rise of cryptocurrencies, such as bitcoin, has resulted in an explosion of ransomware attacks. Cybercriminals like bitcoin payments are difficult to trace and can be transferred electronically without assistance from banks or other regulated institutions. These factors have led to an increase in ransomware attacks.
Ransomware attacks are on the rise
For CNI organisations, ransomware is the top threat. According to a recent UK National Cyber Security Centre (NCSC) report4, 84% of UK CNI providers experienced cyber-attacks in 2020, and 93% of those providers admitted that at least one attack was successful. For these larger organisations and institutions, the aim can include relying on human error to open the backdoors to an attack, blocking access to healthcare, education, or critical government services until the ransom demand is paid. While this threat has always been present, the move to home working has exacerbated the problem. A recent cyberattack on the National College of Ireland and Queen’s University in Belfast5, for example, highlighted the vulnerability of educational establishments now increasing their use of technology to move lectures online for thousands of students.
Ransomware attacks are not a recent trend
Mazars asked leading IT managed service provider Renaissance to provide their industry insights into ransomware.
“Ransomware is not a recent trend and has been around for several years. Whilst the initial focus of ransomware was to encrypt an organisations data and then demand a ransom for it to be released back to the user. Ransomware has developed into an organised industry crime and is now much more intrusive. Typically, a ransomware attack involves cybercriminals sitting within a target environment (e.g., within an organisation’s network environment) for a period, without being discovered and then the bad guys exfiltrate the data and hold the user to two forms of ransom: - try to get you to pay to have your data released and unencrypted, and
- try to get you to pay so that the data is not released online”.
These dangerous forms of cyber-attack require a multi-layered approach beyond running traditional backups and implementing anti-virus solutions. |
How can my organisation prevent a ransomware attack from taking place?
None of the 80 NHS organisations affected by WannaCry had applied the Microsoft update patch advised by NHS Digital’s Care CERT bulletin on 25 April 2017 following the receipt of intelligence of a specific threat from BT on 24 April 2017. Most NHS devices infected were running the supported but unpatched Microsoft Windows 7 operating system6.
Lessons learnt from other ransomware attacks can help to prevent a cyber-attack from happening in the first place. Unpatched systems are not the only known vulnerabilities; organisations must adopt a zero-trust technical and organisational approach:
Refer to the cyber security protect checklist for information on how to minimise cyber security risks. If you are answering no or not sure to any of these questions you may need to review your organisations current approach to cyber security.
Cyber security protect checklist
How to respond to a ransomware attack?
If you think your IT system is infected by ransomware, take the following immediate actions.
- Ask for help. Contact the NCSC, the Gardai.
- Work with an experienced advisor to help recover from a cyber-attack.
- Isolate the infected systems and phase your return to operations.
- Review the connections of any business relationships (customers, partners, third parties) that touch your network.
- Apply business impact assessment findings to prioritise recovery.
- Have a position to take regarding if your organisation should pay the ransom. Even if you decide to pay the ransom, how can you be sure the encrypted data will be released back to you? How will you ensure you will not be targeted again? If your organisation decides not to pay the ransom, what is the risk associated with not paying? How easy will it be to restore the files and data? What happens if you can’t restore the files and data? What steps will you take to minimise disruption during recovery?
The Irish Government, Gardai and the NCSC believe industry and the public should not pay a ransom as there is no guarantee you will get access to your data, and you will be funding cybercriminals. Should your organisation be a victim of a ransomware attack, you must consider all these points.
For the next ten years, cyber-attacks are ranked as the second risk for business globally7. Not only for Ireland’s operators of essential services such as healthcare, education, energy and banking, but for all industry sectors. Now is the time for Irish organisations to act, to prevent or to minimise the disruption from future ransomware attacks.
Sources
- https://www.rte.ie/news/health/2021/0517/1222037-hse-ransomware-attack/
- https://www.bbc.com/news/business-57112371
- https://www.nomoreransom.org/en/ransomware-qa.html
- https://www.ncsc.gov.uk/report/weekly-threat-report-26th-february-2021
- https://www.bbc.com/news/uk-northern-ireland-56287355
- https://www.england.nhs.uk/wp-content/uploads/2018/02/lessons-learned-review-wannacry-ransomware-cyber-attack-cio-review.pdf
- https://www.weforum.org/reports/the-global-risks-report-2020